| P19673 | Security in Building Automation | |
| |
|
Security threats in Building Automation Systems (BAS)To be able to integrate security-critical services, the implemented control functions i.e., functions that control the building automation services have to be protected against unauthorized access and malicious interference (security attack). A typical example of such a security attack is the manipulation of an access control system that opens and closes an entrance door. To perform security attacks, the malicious entity (adversary) has to identify vulnerabilities of a system that can be utilized to gain unauthorized access to the control functions. The existence of vulnerabilities leads to a security threat which can be regarded as the potential for violation of security that may or may not be utilized. Fig. 1 shows the relation between these basic security terms.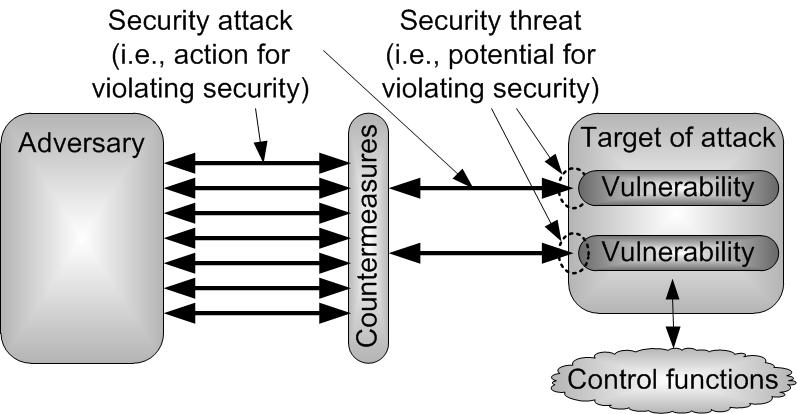 Fig.1 Security attacks On the one hand, the protection of a system against security attacks demands that the amount of vulnerabilities is minimized by incorporating security in every stage of the system's life cycle, especially already during design. On the other hand, countermeasures that eliminate or prevent security threats and attacks in advance have to be implemented. For example, the encryption of transmitted data can be used to avoid a disclosure of confidential information. In cases where a prevention is not possible with reasonable effort, mechanisms trying to at least detect security attacks, report them, and minimize the resulting damage have to be deployed. Consider, for example, an intrusion detection system (IDS) that reveals abnormal system behavior and tries to prevent a propagation by isolating the source of the attack.% Another example is a Message Authentication Code (MAC) that detects an unauthorized modification of a message. Target analysisIn today's BAS, the control functions are distributed to control applications being hosted on different devices interconnected by a common network. Therefore, the adversaries' ultimate goal will be the access to these control applications to be able to manipulate them for their own needs. Unauthorized access by an adversary to control functions can be gained by, on the one hand, directly manipulating the control applications (e.g., changing the control logic or modifying control data such as an output value) or, on the other hand, by indirectly changing control parameters or interfering with the data exchanged among the control applications. %that is exchanged between the control applications. Therefore, the control applications themselves as well as the ways to interact with them have to be secured.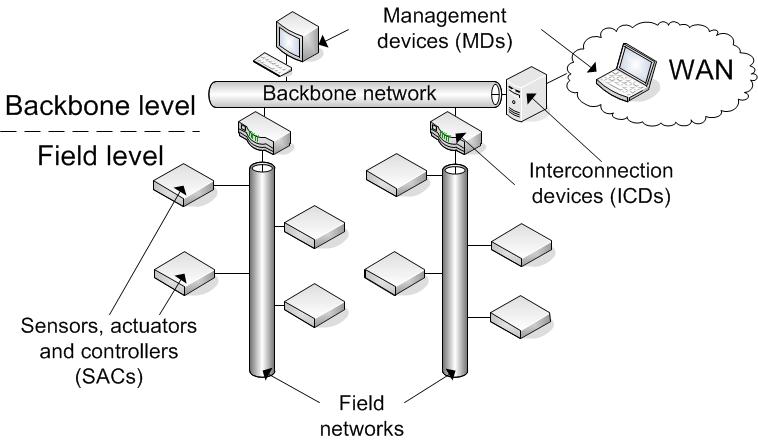 Fig.2 Building automation network The distributed control applications of a BAS are spread over a network called building automation network (BAN). While the functionality of a BAS is organized in a three-level hierarchy, BANs are typically implemented following a two-tiered model (cf. Fig. 2). Field networks are home for sensors, actuators, and controllers. They are interconnected by a common backbone where management nodes that require a global view of the entire BAN are located. With this topology in mind, three different device classes can be identified: Sensors, actuators, and controllers (SACs) that interact with the environment and perform control functions, management devices (MDs) that execute configuration (e.g., set initial configuration parameters), maintenance (e.g., changing setpoints), and operator tasks (e.g., visualization and alarm monitoring), as well as interconnection devices (ICDs) providing an interconnection between network segments (e.g., routers) or remote access to foreign networks (e.g., gateway to a Wide Area Network, WAN). Attack analysisBased on this abstract BAN model, five potential attack targets %to get unauthorized access to the control functions and the following attack scenarios can be identified.
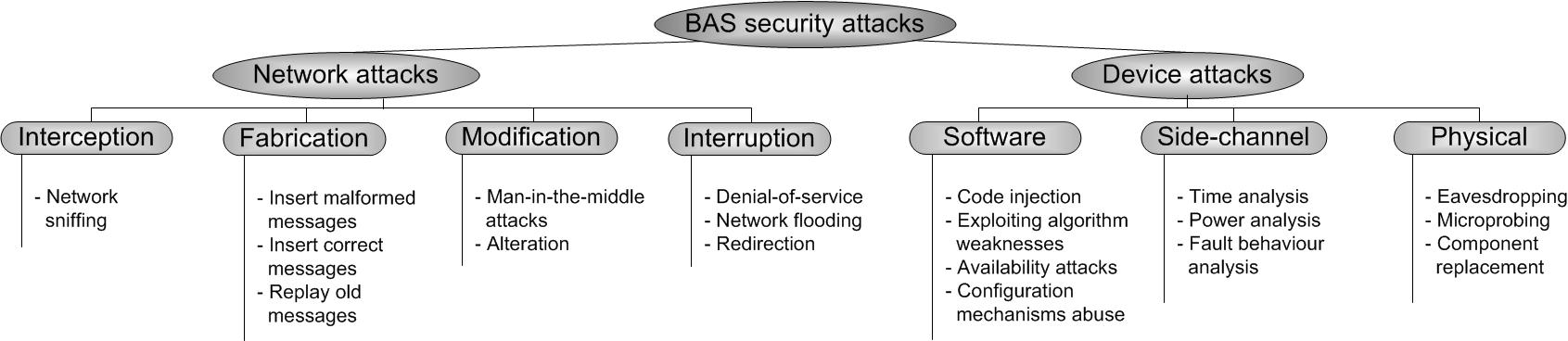 Fig.3 Attacks in building automation systems To sum up, an adversary has two different opportunities for getting access to control functions (cf. Fig. 3). On the one hand, an adversary may attack the network medium to access the exchanged data and thus interfere with the data when it is transmitted (network attacks). An adversary may try to intercept, manipulate, fabricate, or interrupt the transmitted data. While some attacks like network sniffing try to interfere with the transmitted data without altering it (passive network attacks), active attacks alter or affect the data during transmission. Access to the network medium can be achieved in two ways.
On the other hand, the adversary may attack a device to access control functions (device attacks). These attacks can be classified based on the means used to launch them.
Challenges for providing security in BASIn the IT world, many well-established security mechanisms exist. However, they cannot be trivially mapped to the building automation domain for various reasons. Due to cost efficiency, SACs are normally embedded devices with limited system resources (e.g., memory, processing power) that rely on bus- or battery-power. Security mechanisms (especially cryptographic algorithms) are computationally intensive and must not exceed the available device resources. The overhead imposed by these mechanisms needs to be reasonably small. Therefore, a suitable balance between a required level of security and available resources has to be found ("good enough security").For many services in the IT world the amount of devices that communicate with each other is relatively small, thus allowing the client/server model to be used in most cases where only the communication between the clients and the server has to be secured. BANs, on other hand, usually consist of only a few MDs, some ICDs with defined applications, and thousands of manifold SACs. Communication between SACs occurs peer-to-peer based without a central instance. Thus, scalability of the integrated security mechanisms is of major concern. Furthermore, IT security mechanisms are geared towards different requirements regarding the used network technology. While in the IT world IP based network protocols are dominant, the use of IP networks in BANs is reserved to the backbone level. At the field level, predominantly non IP fieldbuses are used. Besides, control data typically transmitted in BANs has a small volume (in the order of bytes) with perhaps soft real time requirements (e.g., reaction time in a lighting system). In the IT/office domain, the data volume to be transferred is commonly high (in the order of mega- or gigabytes) with usually no real time requirements. Moreover, in BANs, devices often operate in untrusted environments where physical access (e.g., an intrusion alarm in a public building or a wireless sensor network) is given. Therefore, it has to be assumed that a short time physical access to devices and networks cannot be avoided. Finally, BAS have to be kept operable for years or even decades. Due to the intended long lifetime, the possibility to update the software running on the devices has to be provided. This update mechanism also offers an additional attack point that has to be protected against unauthorized use. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
With support from |
  |